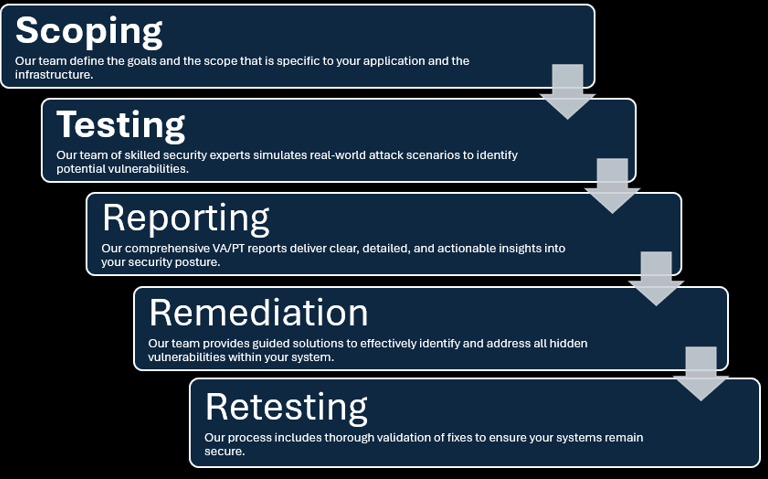
Vulnerability Assessment and Penetration Testing
Vulnerability Assessment and Penetration Testing (VAPT) is a comprehensive approach to identifying and addressing security vulnerabilities within an organization's IT infrastructure.
Industry leaders and analysts recommend that in-house red teams may not be the most effective way to conduct these activities. Instead, it is advisable to engage external experts who possess the specialized skills and impartial perspective necessary for thorough and effective VAPT.
Vulnerability Assessment (VA): This involves systematically scanning and analyzing systems to identify security weaknesses and vulnerabilities. The goal is to detect potential security gaps before they can be exploited by malicious actors
Penetration Testing (PT): Also known as ethical hacking, this process involves simulating real-world cyber attacks to exploit the identified vulnerabilities. The objective is to understand how an attacker could gain unauthorized access and to evaluate the effectiveness of existing security measures
Why VAPT is Important
Proactive Security: VAPT helps organizations identify and address vulnerabilities before they can be exploited, thereby preventing potential security breaches
Compliance: Many regulatory standards and frameworks, such as ISO 27001, PCI-DSS, and GDPR, require regular security assessments. VAPT ensures compliance with these standards
Risk Management: By understanding and mitigating vulnerabilities, organizations can reduce their risk exposure and enhance their overall security posture
Continuous Improvement: Regular VAPT exercises help organizations continuously improve their security measures and adapt to evolving threats
Types of VAPT
Network VAPT: Focuses on identifying vulnerabilities in network infrastructure, including firewalls, routers, and wireless networks
Web Application VAPT: Targets web applications to uncover issues like SQL injection, cross-site scripting (XSS), and insecure APIs
Mobile Application VAPT: Examines mobile applications for security flaws that could be exploited on mobile devices
By leveraging VAPT, organizations can ensure a robust and resilient cybersecurity framework, protecting their digital assets and maintaining trust with their stakeholders.

"VigilUp's VAPT service was exceptional. Their team identified and fixed vulnerabilities efficiently, greatly improving our security."
John Doe

"We were impressed with VigilUp's thorough VAPT service. Their expertise and clear communication made the process smooth and effective."
Jane Smith